A Case Study of Mobile Health Applications: The OWASP Risk of Insufficient Cryptography

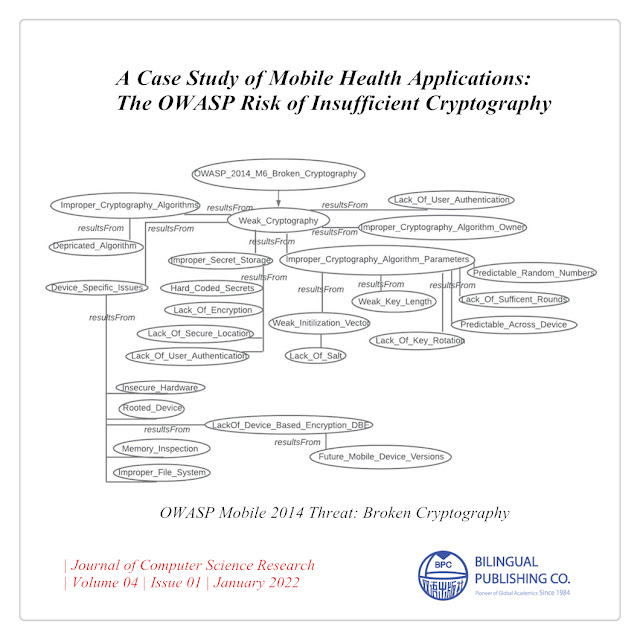
A Case Study of Mobile Health Applications: The OWASP Risk of Insufficient Cryptography DOI: https://doi.org/10.30564/jcsr.v4i1.4271 Abstract Mobile devices are being deployed rapidly for both private and professional reasons. One area of that has been growing is in releasing healthcare applications into the mobile marketplaces for health management. These applications help individuals track their own biorhythms and contain sensitive information. This case study examines the source code of mobile applications released to GitHub for the Risk of Insufficient Cryptography in the Top Ten Mobile Open Web Application Security Project risks. We first develop and justify a mobile OWASP Cryptographic knowledgegraph for detecting security weaknesses specific to mobile applications which can be extended to other domains involving cryptography. We then analyze the source code of 203 open source healthcare mobile applications and report on their usage of cryptography in the applications. Our f...